What is a Trojan Horse Attack?
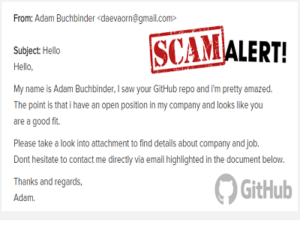
Sample scam mail
A Trojan horse, often shortened to Trojan, is a type of malware designed to provide unauthorized, remote access to a user’s computer.
Suppose you are working in a Bank and you have a communication system like Viber or Whats app to communicate with other colleagues. One day a new message with Hyper Text Link came to your inbox from a colleague subjected “Funny News”. Obviously you will be curious to see that funny news. Once you clicked on that link, a hidden malware installed to your PC. But you did not notice that a program always running behind your system and it allows the hacker to remotely access your PC. By this remote access, that person can transfer all data to his own PC. And using those data, he can harm or black mail you. And it can destroy your professional career in a few second!
How It Works?
In the form of software program, Trojan horses can appear as a game, a mobile application, a utility program, or a textual hyperlink. Each intends to enhance interest and to entice an unsuspecting user to download the disguised malware or virus. Once downloaded and installed, the infection is free to collect personal information, destroy files and records, and eventually render your computer or network unusable. Cybercriminals purposely create malware and virus packages with the intention of either obtaining personal information or destroying computer records and files. By hiding the malicious code and making it appear innocent, many individuals will overlook the possibility of a Trojan horse and download the package without thinking. Keep in mind that Trojan horses can also infect Android and other mobile devices by creating a Trojan horse masquerading as a popular new game such as Angry Birds or an application such as the ‘flashlight’ app.
Adversity of Trojan Horse Malware:
Daily, thousands of computer users unintentionally ingest and launch a Trojan horse malware and infect their home computers and workplace networks. Recently it affects the Github users. Open source developers, using the popular code-sharing site GitHub, were put on alert after the discovery of a phishing email campaign. It attempts to infect their computers with an advanced malware trojan. For Bangladeshi Professionals of Banks and Govt Organizations, this malware can effect disastrously. Because most of the Employees are not aware all those security threats.
Avoiding Trojan:
To avoid Trojan attack you should follow some simple steps:
………Be Careful, Stay Safe………