Update 5 (Monday 16.05.2017 BDT): Now you can add Bangladesh officially to the list of affected countries suffering from this ransomware. Number of affected workstation or laptops varies from 30-50.
If you still haven’t install patches that has been released to solve this issue. Please do it now. And refrain yourself from clicking any link coming through mail unless you are absolutely sure of its authenticity and integrity.
Update 4: So far WannaCry ransomware has infected over 213,000 Systems all over the world. To get live updates of this attack follow this link
Intel MalwareTech Live Tracker
Update 3: It is not over yet. Actually it is far from over! Attacker have released a new upgraded version of Wanna Decryptor or WannaCryptor named as WannaCry 2.0 with no ‘kill-switch’ functionality.

Image: thehackernews.com
If you still haven’t installed these just released patches, please do it now.
Or better, you can disable the SMB functionality on your system altogether. Just follow these steps.
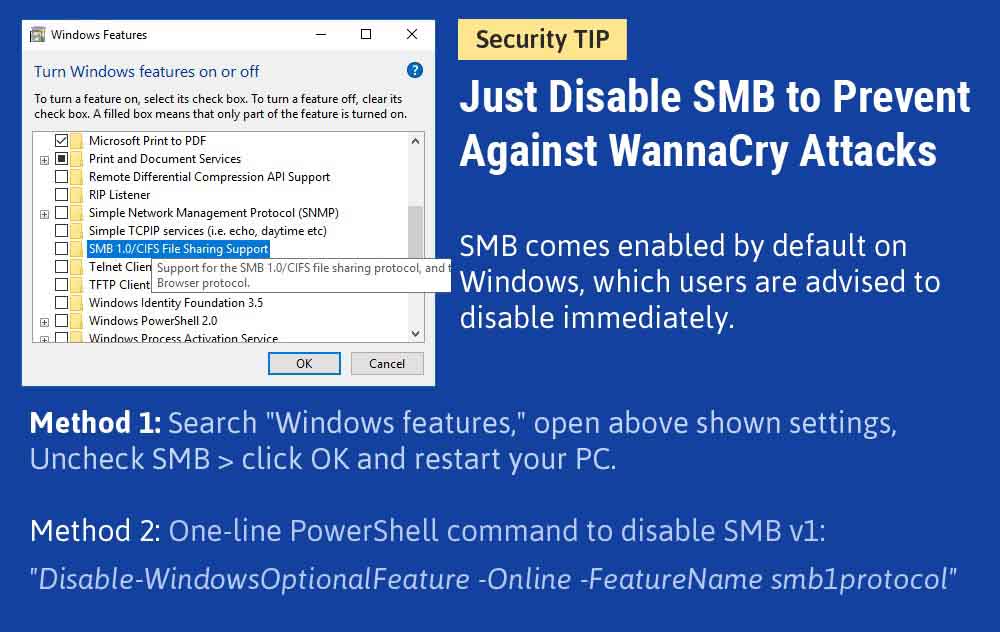
Image: thehackernews.com
Update 2: Understanding the seriousness of the issue, Microsoft released patches for all its unsupported version of Windows, including Windows XP, Vista, Windows 8, Server 2003 and 2008 to fix that particular issue.
So if your organization is still using one these systems, please update it now. If you are not using these systems but have not updated your systems for a while- DO IT NOW.
Update 1: The attack was accidentally slowed down when a researcher registered a domain that appeared in the source code of ransomware. That security researcher named MalwareTech found that it is possible to activate the kill switch by registering the web domain and posting a page on it. Fortunately, it did the trick.
Security firm Malwarebytes and Cisco’s Talos security group reported the same findings and said new ransomware infections appear to have slowed since the kill switch was activated.
Full Report here on their blog.
End of updates. Original news starts from here:
On May 12, 2017 a world-wide outbreak of a Ransomware came to our attention. This attack appears to be spreading around everywhere, using a hacking tool which was dumped by a hacking group over a month ago.
This ransomware, called Wanna Decryptor or WannaCryptor, struck hospitals at the U.K.’s National Health Service on Friday, taking down their network. In addition to that, multiple global organizations around the globe are also experienced this ransomware attack.
Currently it’s moving like a wildfire. There are several reports of attack across 74 countries in more than 45,000 attacks.
According to Kaspersky’s Twitter post, some of the countries that have been hit include Britain, Spain, Russia, Taiwan, India, and Ukraine.
Now if you unaware or not well-versed on about Ransomware. Let us give you a quick overview.
According to Wikipedia,
“Ransomware is a type of malicious software that carries out the cryptoviral extortion attack from cryptovirology that blocks access to data until a ransom is paid and displays a message requesting payment to unlock it. Simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse. More advanced malware encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them”
To summarize, its stops you from using your PC. It holds your PC, Laptops, Workstation, Mobile devices or important files for “ransom”.
The most obvious way to know if your computer has been affected is, whether you are seeing a ransomware pop-up screen when you start up or using your machine. Like the following screenshot (it was taken from a system which was affected by the current attack)
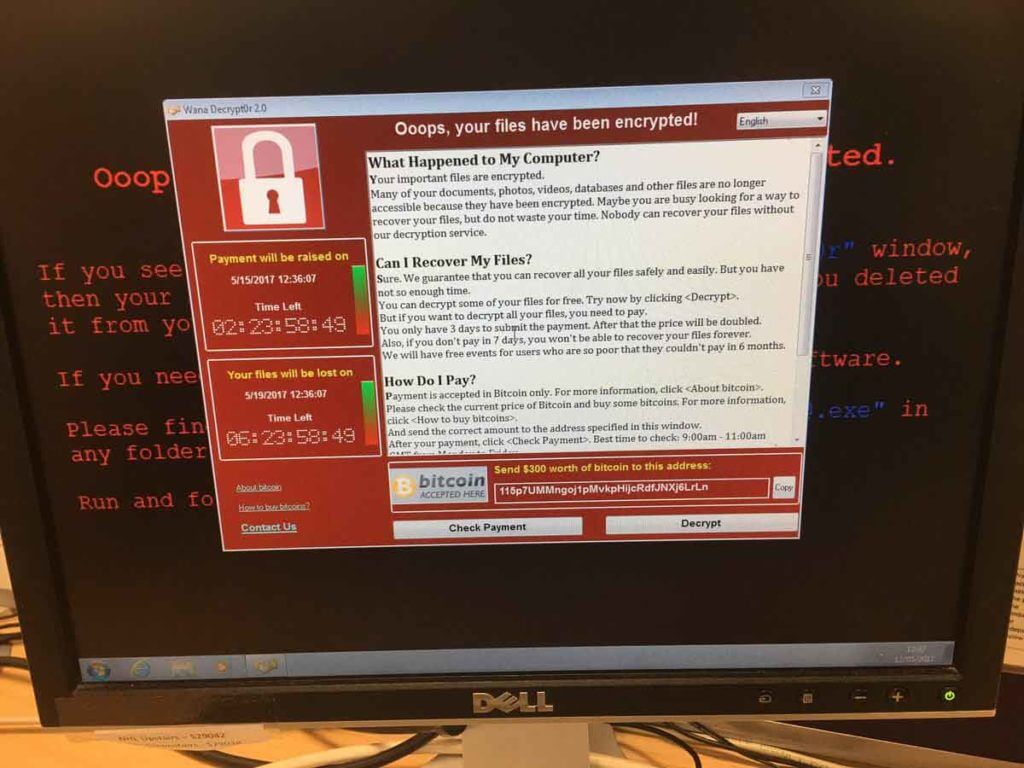
Image: Twitter
How it’s happening?
This attack is utilizing Windows SMB security vulnerabilities to infiltrate the network or system.
We already did a news on this particular issue few weeks ago. Microsoft did also released their patch in March to combat this issue. But due to user or organizations lack of awareness about it and Microsoft itself discontinued releasing update of older machines like Windows XP (which unfortunately lots of organizations are still using) and such, hackers are now able to attack networks, organizations using this flaw and held them to a ransom.
The attack can happen in various ways, from link within an email or documents such as PDF among others which starts the infection chain.
The best way to stay safe from this and any other cyber attack in future, is to install patches regularly whenever there is one. Same goes with Antivirus. Update as soon as there is new virus definition or signature has been released.
Thank you for being reading this article.
Stay safe.