In traditional security assessment, security professionals try to conduct penetration test, ethical hacking and so on. The security professionals think that if they can find vulnerabilities via conducting bug bounty or penetration testing, those vulnerabilities can be fixed and they are secure from cyber-attacks. But the real hacking is often quite different from penetration testing attacks, ethical hacking or this kind of staffs.
In reality, most of the modern attackers does not use system or application vulnerabilities as their initial entry point for any target organizations. Because it is very complex and time consuming to find the real vulnerabilities. Sometimes there is no exploitable vulnerability for initial foothold in target network. The attackers tend to use vulnerable people instead of IT infrastructure vulnerabilities. They try to use targeted phishing or spare phishing attacks. Because Human manipulation is easier.
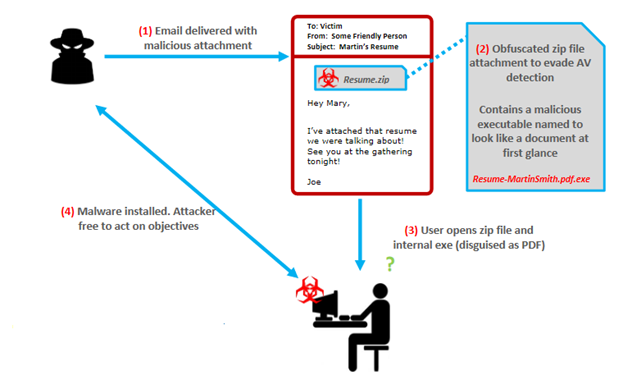
Getting the initial entry points
Well, we know human is vulnerable most of the times. This allows the attacker use sophisticated phishing or spear phishing attacks for initial entry. For example, office employees frequently use LinkedIn or Facebook in office computer or corporate networks. Sometimes they click different links, such as job offer, or others link which is looks like quite legit. As a result, it is possible that a malware is executed via macro documents or others file less malware or PowerShell commands which undetectable by traditional security control. Then the attacker execute a series of commands by macro and download malware. This way, the attackers easily get their initial entry point of their targeted organization’s network. After initial foothold, the attacks act as APT (Advance Persistence Threat).
Getting administrative privilege
Most organizational users use windows OS as their workstation operating system. If attackers can compromise any admin users via phishing as we discussed earlier, they can get privileged user access. Some windows application needs administrative ACL permission for administrative activities, such as “run as admin”. And some special application like- system32 applications does not need any ALCs. Attacker forge them to execute their malware or download the malware. Eventually the attacker gets complete control of that user’s workstation. Sometimes attackers create command and control (C&C) server for execution of further instructions.
Lateral movement
Once the attacker can get a machine fully compromised, the attackers try to move horizontally and try to find IT admin or domain controller machine. If attacker can compromise the domain controller, the attacker gets the power to control everyone.
Data exfiltration
After getting all access over the organizations, the attacker can steal data or destroy the sensitive data which is extremely risky and dangerous for any organization.
Recommendation
As we discussed, the phishing attack or social engineering attack is the initial footstep for an attack. To get rid of this, the organization must educate their employees regularly and improving employee security awareness. Once the organization detects cyber attack activities, organization can use Breach Detection System (such as: Trend Micro Deep Discovery Inspector). Organization alsocan run Breach and Attack Simulation (such as – PICUS Security) program frequently, so that they can measure their people, process and technology. Also they can measure their security policy.
Summary
In this discussion, we tried to educate you on how attacker gets into the secured networks. Social engineering is a widely used method in modern cyber-attacks or targeted attacks. The Attackers develops special malware based on their target organization. So if we need ensure our protection we must change our traditional protection approaches.