Greetings! Today were are here with the details about a very risky malware. Cyber threat landscape is changing rapidly every day. It is an undeniable fact that cyber criminals are becoming more organized, skilled and innovative as technology progresses. These hackers are taking better strategic approaches and becoming more sophisticated and creative in their methods of attack.
New attack patterns are having stealthier techniques that involve manipulation of standard system tools and protocols some of which are not always monitored. A new hidden attack formed in Microsoft Word has been found recently.
This fileless attack has been discovered by the Cisco Systems Talos team researchers. The DNSMessenger malware driven attack targets Microsoft Word via a malicious document that is propagated through an email phishing campaign. This technique is extremely difficult to identify.
A security researcher (@simpo13) initially identified this malware. He notified Talos about one peculiar bug of the code that he discovered. It calls out Cisco SourceFire security appliances with the encoded text, “SourceFireSux.”
The Trojan came into the consideration of Cisco’s Talos team who highlighted a tweet that encoded message in a PowerShell script that said “SourceFireSux.” SourceFire is one of the corporate security items of Cisco.
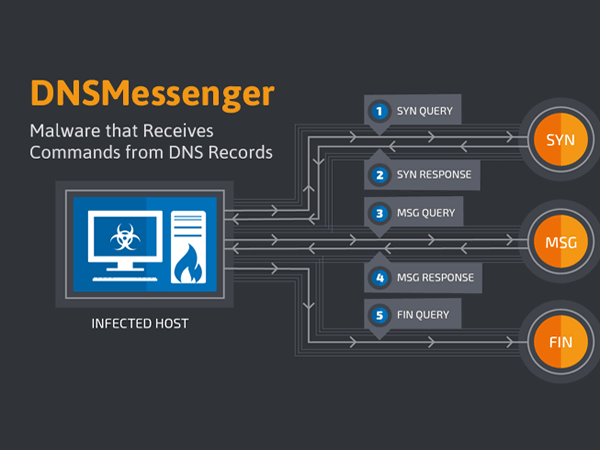
After preliminary analysis, Talos scientists came across a hostile attack against Word record and a PowerShell backdoor access speaking with its C&C (Command & Control) servers through DNS requests.
It is important to mention that DNS is normally used to look up the Internet Protocol addresses associated with domain names, but it has support for different types of records. The TXT record in particular allows a DNS server to attach unformatted text to a response.
DNSMessenger Powershell Fileless Malware
Of course, email phishing is hardly a new concept. Phishing involves the attackers simply sending out thousands of emails with infectious attachments. The attacker is literally fishing for someone to take bait, usually a vulnerable user who would open an anonymous email.
DNSMessenger is cleverer because the malicious attachment is stealthier. It pretends to be a protected document that has been secured by reputed security firm McAfee. However, it is not really secured by the Intel Security-owned company. Many users may be duped by the masquerade and click the enable content button that is provided.
The attack script is written in Powershell, a powerful scripting language built into Windows platform for the automation of system administration tasks. Until this point of attack, everything is done in memory, without writing any malicious files to disk.
The second stage is also done using Powershell and involves checking for a number of parameters of the system environment. These parameters include the privileges of the logged-in user and the version of Powershell installed on the system. This information is used in deciding the strategy for proceeding to the next step and how to achieve persistence in the system.
This data is then used to guarantee perseverance on the tainted host by changing the Windows Registry and introducing a third stage PowerShell script that contains a basic secondary passage through backdoor. The backdoor is being added to the Windows Administration Instrumentation (WMI) database, if the casualty has administrative rights, permitting the malware staying persistently even after a reboot. This Backdoor is an additional script which create a complex 2-way communication channel over DNS system. It is usually used to look up the IP addresses associated with domain names, but has support for different types of records.
The DNSMessenger malware backdoor uses DNS TXT records that, by definition, allows a DNS server to attach unformatted text to a response. Now, this “fourth stage” Powershell script is the actual remote control tool used by the malware attacker. This script queries the command-and-control servers via DNS TXT message requests to ask what commands to execute. Any command received is then executed, and the output is communicated back to the C&C server, allowing the attacker to execute any Windows or application commands on the infected system.
This is not the first time when the researcher discovered a fileless malware. Earlier last month, Kaspersky researchers also discovered fileless malware, that resides solely in the memory of the compromised computers, targeting banks, telecommunication companies, and government organizations in 40 countries.
Good luck and of-course keep in touch with us for latest updates. Bye..