
Let’s start with few questions first before we dive deep into corporate security.
Do you know it is extremely risky to have one or two familiar passwords that you use repeatedly for most, if not all, of your personal online accounts as well as on your corporate environment?
Do know it is highly recommended that you don’t turn off the regular update feature of your computer and smartphone even if it takes too much space and bandwidth for your liking?
Do you know what the term Social Engineering actually means?
Even if one of your answer for the above questions is “No”. It is essential that you read rest of this article in order to know the common corporate security risks and how to avoid those.
1. Password Dilemma
I will talk about this problem on two parts.
Firstly, I will try to give some insights on the matter of weak password. It takes as long as 0.86 seconds for a hacker to crack your password if its length is only 3. See the figure below for more information

So as you can see, the shorter the password is, the easier it is to crack. And let’s be honest here, we LOVE using short passwords for various reasons. Mostly because it is easy to remember. In addition to that, it is easier to type out a shorter one than a long password.
Now let’s dive into second part of this discussion. Misuse or over-use of a password. It is safe to say most of us have one or two favorite passwords that we use repeatedly basically everywhere. It’s always risky to do that. Because if one somehow get hold of one of your password, the person can practically hacked through all your account that exist online.
Now combine these two above facts altogether, you have a set of weak password and you are using it over and over again on different platforms. Consider the consequences one have to face if somehow one of his/her account gets hacked. Losing one’s hard earned money, sensitive private information and what not! Now imagine the consequence when it happens to one of your accounts which is linked to your corporate environment.Best case scenario? Losing handful amount of money, reputation and important information which will hurt your corporation on the long run. Worst case Scenario? Its not that hard to imagine!

So now the question arises how can you remain safe from all of this?
It is not that hard actually.
A good password would normally consists of numbers, letters with both upper and lower cases, special symbols. Another information which is quite important is that, the length of a good password would normally be at least of 8. To crack a password of length 8, can take up to 2.10 centuries assuming you implemented the good password rule mentioned above. So as you can see the longer your password gets, the harder it becomes to crack.
Before ending, just want to mention a point, using a direct word from dictionary (doesn’t matter how long it is) to make a password is really not recommend for anybody. Just Google the phrase “dictionary attack“, you will understand.
Last but not least, always activate 2-way authentication process whenever possible, not only for corporate security.
2. Failure to Update Software Regularly
It is very common in our country to disable the auto-update feature of software after we install it. This is true for both corporate and social environments. This is done mostly to save storage capacity and reduce bandwidth consumption. As a result, that leaves our devices exposed to different kind of security threats and attacks which could have been easily avoided by installing regular automatic updates and patches. These updates and patches are released for repairing various security holes and bugs left in the initial releases, along with other fixes.
As I have just mentioned a moment before, the solution is very easy and obvious one. Just install updates as soon as humanly possible. And to ensure corporate security, it is a MUST.
3. The True Nature of Social Engineering
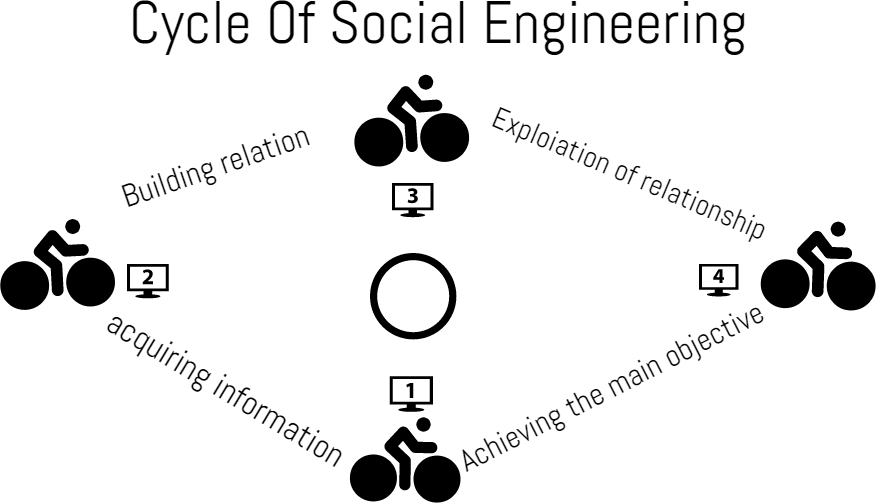
If you don’t know it already, it may come to you as a surprise. The term “Social Engineering” refers to manipulating people into doing something illegal or giving sensitive information to the wrong person. The form of manipulation can come in very different ways. Some of them are mentioned below.
There are many more but in way they all are similar in terms nature of the attack.
4. BYOD Policy and Its Affects
As more corporations and organizations are embracing BYOD policy (Bring Your Own Device) day by day, the risk of security breaches and vulnerabilities are increasing accordingly.
Data theft is at high vulnerability when employees are using mobile devices [particularly their own] to share data, access company information, or neglect to change mobile passwords,†explains Jason Cook, CTO & vice president of Security, BT Americas.
According to a BT study, mobile security breaches have affected more than two-thirds (68 percent) of global organizations in the last 12 months.
Most of the phones are now being rooted or jail braked. Plus the increased use of proxy servers to bypass company policy have all but signifies the risk more.
The solution for this particular complex problem is, educate employees properly on security matters and threats as well as on company policies regarding this issue. Implementing a monitoring system to monitor online activity would be good option too.
5. Inappropriate Security Controls/Privileges
It is another major security concern that most of the corporations or organizations ignore deliberately knowingly or unknowingly. To make things less complicated for end users, admin of the system either give unnecessary high privileges to non-deserving users or worse, disables security controls that is essential to prevent security attacks. Another major problem related to this particular issue is, web surfing from admin account. It does nothing but only increases the risks of security attack.
The fix is simple. Forbid web surfing from the accounts of administrators. Provide high privileges to accounts only those who deserve it.
These are some of the most applicable corporate security risks in our country. Suffice to say, these are not the only ones. There are more. But these are certainly most relatable ones in terms of our country’s corporate infrastructure. I will try to cover some more concerning issues in future.
Thank you for reading it.