What Is Caller ID Spoofing?
Public telephone networks usually provide Caller ID information to the receiver during call these days. Caller ID information includes the caller’s name and phone number. However modern technologies like VoIP can allow callers to forge Caller ID information and present false information to the receivers. Gateways between networks allow such spoofing and the adjacent public networks then forward this false information to the receiver.
Spoofed calls can be originated from other countries and as a result, the law of the receiver’s country may not apply to the caller. This limits the effectiveness of law against the use of spoofed Caller ID information to further a scam.
Caller spoofing, also known as Caller ID faking, is widely used for hiding caller’s information and providing fake identity during calls.
Is It Legal?
In many countries (including the US) spoofing caller id “with the intent to defraud, cause harm, or wrongfully obtain anything of value” is absolutely illegal and the crooks can be prosecuted.

But that does not stop legitimate companies from trying to find loopholes. For example, the New York Times used to spoof their outgoing phone calls with the number 111-111-1111 so that the reporters’ phone numbers would not appear on their “anonymous sources” call logs. They intentionally masked the phone number to avoid disclosing sources. They abandoned the practice once the US starting cracking down on call spoofing.
How Caller ID Spoofing Works?
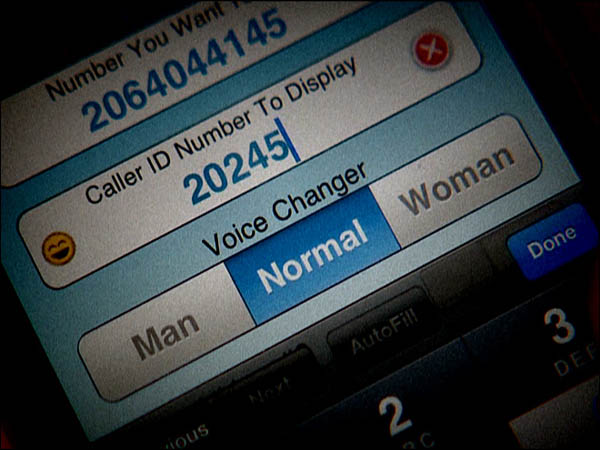
Outbound Caller ID can be spoofed in a number of ways. The most popular, and easiest of one is done through Voice Over Internet Protocol. VoIP is the technology that allows voice communication to be conducted over Internet. Some VoIP providers allow their users to configure the number they display as the caller ID. It can be done through the configuration page on their website.

In VoIP based spoofing services, the call flow can be described as follows: The user opens the application (web or mobile) of the spoofing provider. They enter the number they wish to call, followed by the number they wish to display at the receiving end. When they press ‘send’ or ‘call’, the call is sent through a VoIP service, where the outbound caller ID is changed and then the call is connected to their desired number.
Other spoofing services use a personal identification number (PIN). Users dial a number to connect to the service and enter their PIN. Then they enter the number they wish to call, followed by the number they want to display as their Caller ID. When the call is connected, the receiver sees the caller ID which the caller has chosen to display as their outbound number.
History of Caller ID Spoofing
In the 1990’s, people with a Primary Rate Interface had an Integrated Services Digital Network. This was a special digital connection from their telephone service providers which offered them the ability to change their outbound caller ID. During that time, caller ID spoofing was used primarily by law enforcement officials, private investigators and collection agencies.
In 2005, SpoofCard changed the entire caller ID spoofing landscape when it launched with more features, a better interface, and greater reliability – all at a better price than other companies in the spoofing industry.
In 2006, Paris Hilton used Caller ID spoofing to navigate her way into the voicemail of Lindsay Lohan. Since then, caller ID spoofing has been known to be used for malicious purposes, such as telemarketing, prank calls, and swatting.
Types of Scams Fraudsters Do with Caller Id Spoofing
Caller ID Spoofing opened up the doors to so many fraud scams. Some of those scams include:
Account Takeover and Phishing: Where fraudsters call the bank spoofing a real customer’s phone number and social engineer the customer service associate to make them believe they are the real customer. The end result is your bank account is drained in minutes.
Grand Parent Scams: Scammers use the software to pretend that they are the grandchild saying they are in trouble and need money urgently. 9 times out of 10 the elderly grandparents fall for it.
Collection Call Scams: When the fraudsters pretend they are calling from a Payday lender and advising unknowing borrowers to wire transfer money to crooks rather than paying their accounts.
Phishing Bank Details: When fraudsters impersonate your bank phone numbers to call you and then get key banking details from you so they can drain the money from your account.
Police Impersonation: When fraudsters spoof police department phone numbers to threaten or get personal information from unsuspecting victims.
The degree and number of scams are endless and fraudsters are constantly thinking of new and bizarre ways to scam unsuspecting consumers and banks.
Real World Examples
Earlier this year, a tax scam in Pottsville, PA, claimed to arrest victims if they didn’t pay outstanding tax debts. The caller ID that was spoofed showed that the originating call was from a Pennsylvania phone number: 570-622-1234. This number belonged to Pottsville City Hall, giving a false sense of security to anyone who received the call. The police warned of the scam and reminded Pottsville citizens to never give out any personal information over the telephone.

Recently In Bangladesh some Fraudster spoofed calls to some of government professionals and hijacked approx. BDT five million.
How to Protect from Caller Id Spoofing?
Caller Id Spoofing might affect an organization hazardously rather than to a person. An organization can be secured by following some simple rules.
For Banks or Other Financial Organizations
Last Few Words
Do not place all your trust in the Caller ID information presented to you. Now you know that this information can easily be spoofed by the use of 3rd party Caller ID spoofing services and other tools. You should be verifying the caller before doing anything after receiving an unusual phone call.
Please do not forget to read our other articles.
Stay Safe, Keep Safe.